So, there isn’t a good post for this right now. I’ve spent a little time on this server rebuild looking at the options. I have some base assumptions
- Only TLS 1.2 because all other protocols are considered weak at this time.
- Maximum key strength possible – prefer 256 bit ciphers and fall back to 128 bit for software that doesn’t support that.
- Support only the latest OS/Library implementations. That means old version of Java, Android, Windows, OpenSSL etc are not supported.
- Support HTTP/2 You can see the result of my configuration here.
listen [::]:443 ssl http2 default_server;
ssl_protocols TLSv1.2;
ssl_ciphers ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:!DSS:!aNULL;
ssl_ecdh_curve secp384r1;
ssl_prefer_server_ciphers on;
ssl_dhparam /etc/ssl/dhparam.pem;
ssl_session_cache shared:SSL:40m;
ssl_session_timeout 21h;
ssl_session_tickets off;
ssl_buffer_size 4k;
ssl_stapling on;
ssl_stapling_verify on;
resolver 127.0.0.1;
add_header Strict-Transport-Security "max-age=31536000; preload" always;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Frame-Options SAMEORIGIN;
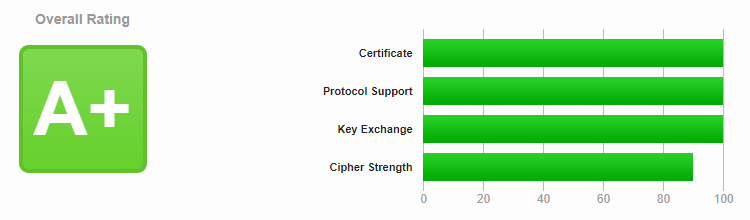
This will give you an A+ with 100% in everything except Cipher Strength. The reason for this is HTTP/2. If you decide you can live without HTTP/2, then remove ECDHE-RSA-AES128-GCM-SHA256 and you will get 100% across everything, but you’ll also break Java8 clients. Which you may not care about.
Letsencrypt certificates should be generated with --rsa-key-size 4096.
dhparam.pem should be generated with 4096 bits also.
